IPSEC is a framework for security that operates at the
Network Layer by extending the IP packet header (using additional protocol
numbers, not options). This gives it the ability to encrypt any higher layer
protocol, including arbitrary TCP and UDP sessions, so it offers the greatest
flexibility of all the existing TCP/IP cryptosystems. Flexibility, however,
often comes at the price of complexity, and IPSEC is not an exception.
Configuring which addresses and ports to encrypt using which IPSEC options
often begins to look like configuring packet filtering, then add in the
additional complexities of key management. While conceptually simple, setting
up IPSEC is much more complex that installing SSH, for example.
What IPsec Does
IPsec provides security services at the IP layer by enabling
a system to select required security protocols, determine the algorithm(s) to use
for the service(s), and put in place any cryptographic keys required to provide
the requested services. IPsec can be used to protect one or more
"paths" between a pair of hosts, between a pair of security gateways,
or between a security gateway and a host.
(The term "security gateway" is used throughout the IPsec
documents to refer to an intermediate system that implements IPsec protocols. For example, a router or a firewall
implementing IPsec is a security gateway.)
The set of security services that IPsec can provide includes
access control, connectionless integrity, data origin authentication, rejection
of replayed packets (a form of partial sequence integrity), confidentiality
(encryption), and limited traffic flow confidentiality. Because these services are provided at the IP
layer, they can be used by any higher layer protocol, e.g., TCP, UDP, ICMP,
BGP, etc.
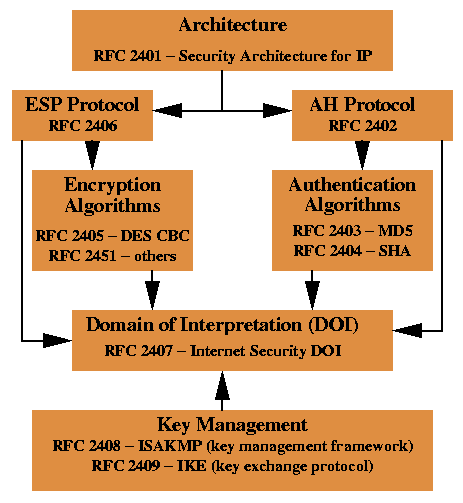
How IPsec Works
IPsec uses two protocols to provide traffic security -- Authentication
Header (AH) and Encapsulating Security Payload (ESP).
The IP Authentication Header (AH) [KA98a] provides
connectionless integrity, data origin authentication, and an optional
anti-replay service.
The Encapsulating Security Payload (ESP) protocol [KA98b]
may provide confidentiality (encryption), and limited traffic flow
confidentiality. It also may provide
connectionless